Stay secure and compliant with our fast and accurate endpoint security audit
Our Endpoint Audit service provide accurately audits your workstations, laptop and server configurations to validate compliance with industry standards in minutes. And if industry standards don’t meet your needs, we do custom audits that you want, quickly and easily.
Audit every endpoint accurately, every time
Our endpoint audit and analyzes the build configurations of your endpoints with the expertise of a skilled penetration tester – saving IT auditors up to 3 hours per audit, per endpoint. Instead of spending time investigating false alerts of non-compliance, we enables you to dedicate your valuable resources to analyzing and prioritizing fixes to secure your servers, workstations and laptops by providing:
Visibility of actual network vulnerabilities including existing false-negatives
Significantly fewer false-positives to investigate
Automated risk prioritization
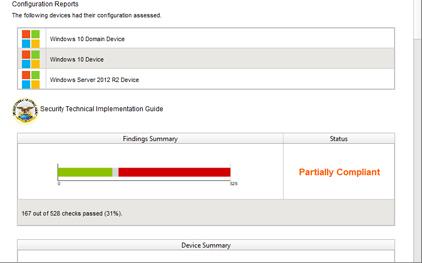
Detailed compliance validation
Flexible, configurable easy to read reports

' Out of the box' auditing
- Device configuration audit
- Pre-defined compliance policies
- Self certification auditing

Custom policy editor
- Customize existing policies to audit against
- Industry standards included (Cyber Essentials, CIS, STIG and NERC)
- Create your own policy for ultimate flexibility

Accurate reporting
- Easy to read reports written in plain English
- Mitigation advice helps you to prioritize and plan fixes
- Machine consumable outputs for system integration
![]()
![]()
![]()