Advisory Services » SOC 2 Assessment
SSAE 18 / SOC 2 Assessment
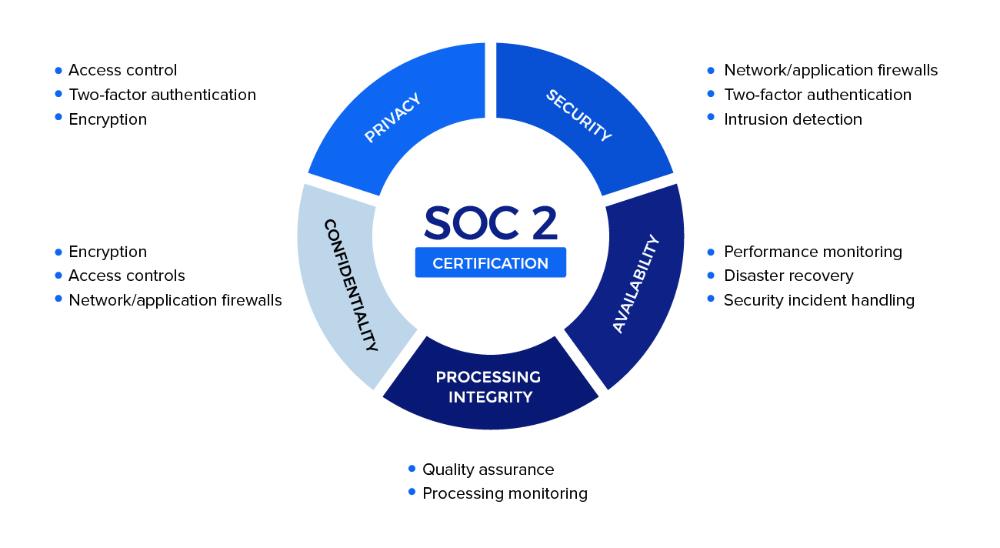
Service Organisation Controls aims to protect the interest of the user entity while receiving services from the service organisation. There are five Trust Services Principles, or criteria, that comprise a SOC 2 report: Security, Availability, Processing Integrity, Confidentiality and Privacy. Essentially, the provider looks at the requirements, decides which ones are relevant to their business practices, and then writes their own controls to fit those requirements. The data provider can write extra controls as needed, and disregard others if they are not relevant to what they are doing if they so choose. The SOC II audit is simply the auditor’s opinion on how that organization’s controls fit the requirements. This makes the auditor’s reputation very important to SOC II reporting, because an auditor who has had many years of experience in SOC reporting will more likely have a more thorough understanding of SOC controls and the best practices to apply to them. The end result of a clean (passed) opinion is that, according to the auditor, the data provider can be trusted as a secure hosting company.
What’s in a SOC 2 report?
There are five Trust Services Principles, or criteria, that comprise a SOC 2 report: Security, Availability, Processing Integrity, Confidentiality and Privacy. Unlike PCI DSS, which has very explicit requirements, SOC 2 requirements allow more flexibility for the data provider to decide how it wants to meet the criteria. Therefore, SOC II reports are unique to each company. Essentially, the provider looks at the requirements, decides which ones are relevant to their business practices, and then writes their own controls to fit those requirements. The data provider can write extra controls as needed, and disregard others if they are not relevant to what they are doing if they so choose. The SOC II audit is simply the auditor’s opinion on how that organization’s controls fit the requirements. This makes the auditor’s reputation very important to SOC II reporting, because an auditor who has had many years of experience in SOC reporting will more likely have a more thorough understanding of SOC controls and the best practices to apply to them. The end result of a clean (passed) opinion is that, according to the auditor, the data provider can be trusted as a secure hosting company.
Earlier known as SAS 70 reports, then SSAE 16 and now SSAE 18, these SOC compliance reports are being used for several years for internal controls, security, processing integrity and SOX compliance. The SSAE 18 Auditor or SOC Auditor is also known as a "Service Auditor". The SOC 2 compliance report mirrors ISAE 3000. The SSAE 18, SOC Auditor can issue a joint SSAE 18 SOC Compliance and ISAE report. SSAE stands for Statement on Standards for Attest Engagements. SSAE 18 is the new standard for all SOC reports. In fact all SSAE including SSAE 16 got merged in the SSAE 18 standard. So we cannot compare SSAE 16 vs SSAE 18. A SOC compliance report is technically an "Attest Report". The "SOC Certification Audit" is a " SSAE 18 SOC Attest Report", SOC 2 Type 1or Type 2 for a vendor or third-party or SOX compliance. A Type 2 compliance report is valid for 6 months or 12 months. For the misisng period, a SOC Bridge Letter for SOC Type 2 may be issued by the Service Organization.
Who Should Obtain SOC 2 Report
As a service provider, you need to guarantee your customers that your IT controls are aligned, designed and applied effectively to its control objectives. Also, any organization that wants to put their information systems up against best practices and those who may use this report to ensure that they have controls to provide security, confidentiality of stored information, processing integrity of transactions, system availability and privacy. Many organizations are good candidates for a SOC 2 report and we provide services not limited to the following industries:
- Hosting providers (web hosting, e-mail hosting, document storage, backup service providers, cloud computing, dedicated server, network administrators, and more)
- Production printing (direct mail marketers, print and mail providers)
- Software as a Service (SaaS)
- Infrastructure as a Service (IaaS)
- Application Service Providers (ASP)
- Health care service providers




